Tryout
This page explains how to onboard API consumers using the Dynamic Client Registration API.
Before you begin:
See the Configurations section and configure Dynamic Client Registration.
Step 1: Deploy the Dynamic Client Registration(DCR) API¶
-
Sign in to the API Publisher Portal at
https://<APIM_HOST>:9443/publisherwithcreator/publisherprivileges. -
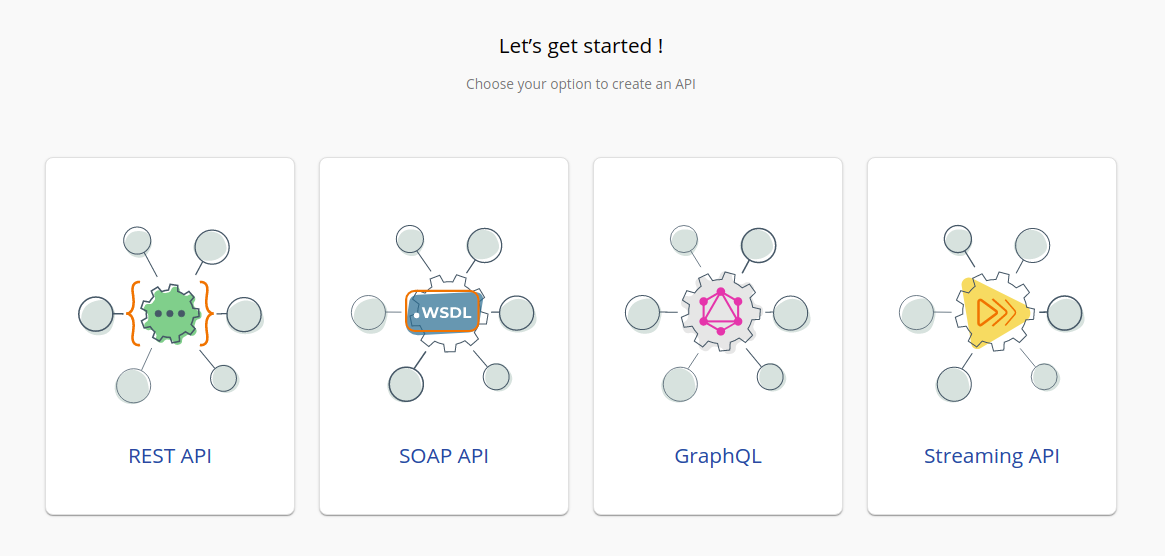
In the homepage, go to REST API and select Import Open API.
-
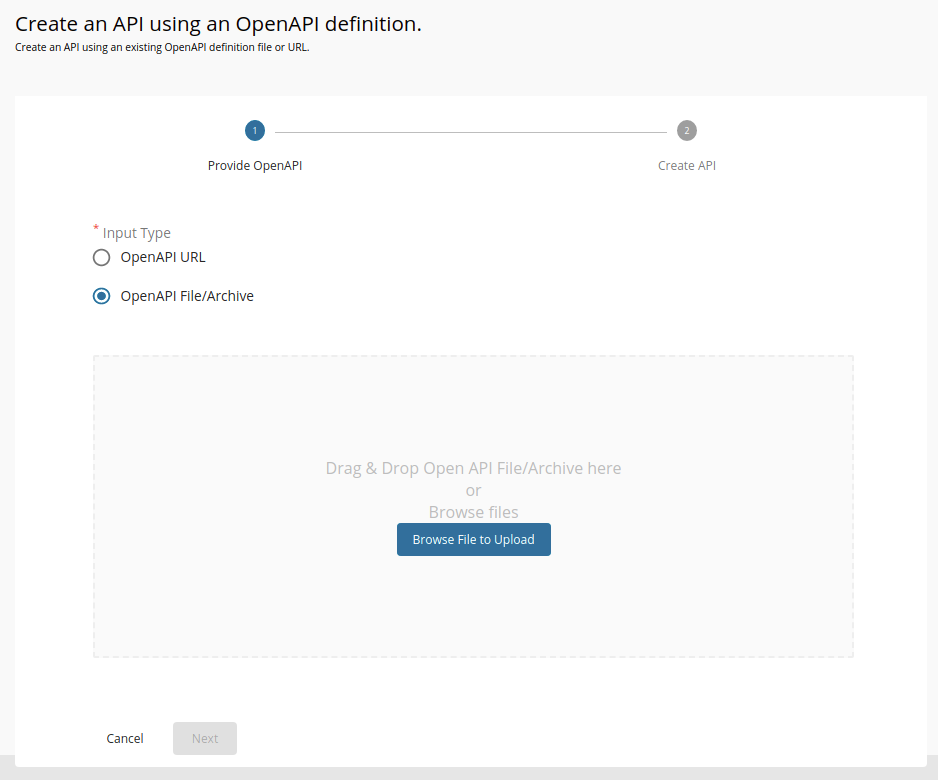
Select OpenAPI File/Archive.
-
Click Browse File to Upload and select the
<APIM_HOME>/<OB_APIM_ACCELERATOR_HOME>/repository/resources/apis/ DynamicClientRegistration/dcr-swagger.yamlfile. -
Click Next.
-
Set the value for Endpoint as follows:
https://<IS_HOST>:9446/api/openbanking/dynamic-client-registration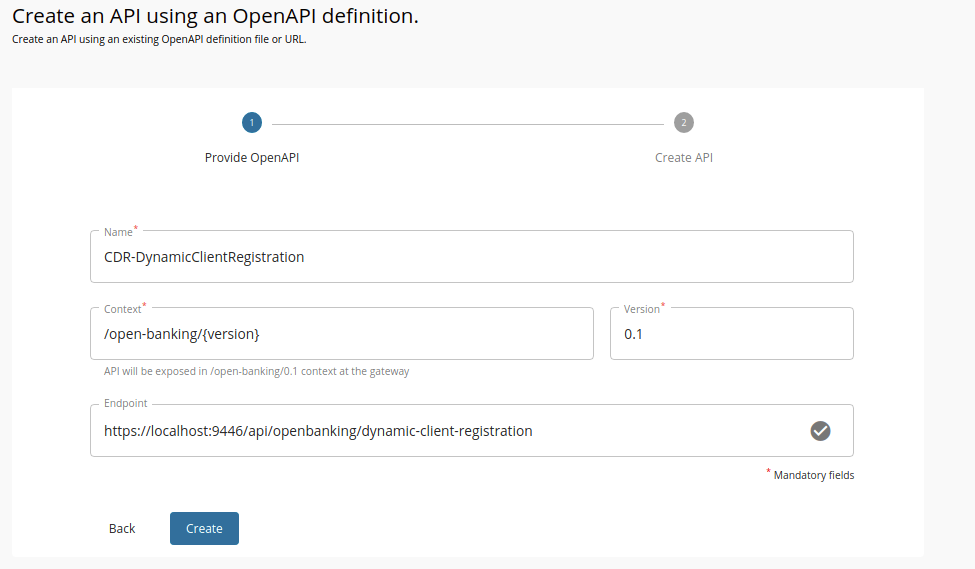
-
Click Create.
-
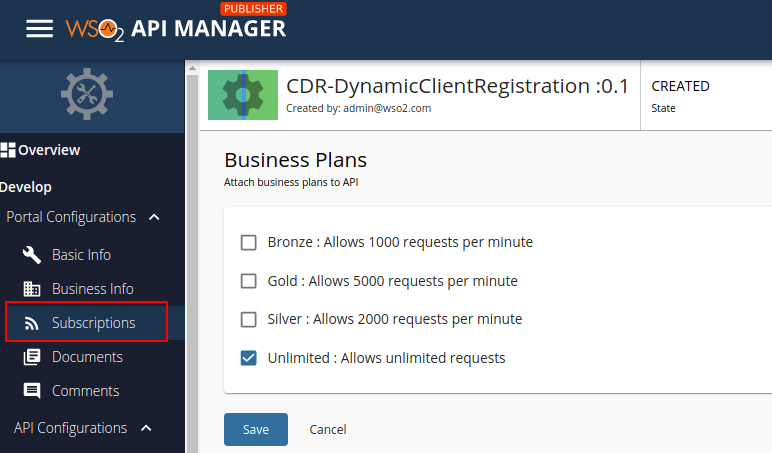
Select Subscriptions from the left menu pane and set the business plan to Unlimited: Allows unlimited requests.
-
Click Save.
-
Go to Deployments using the left menu pane and select Default Hybrid API Gateway.
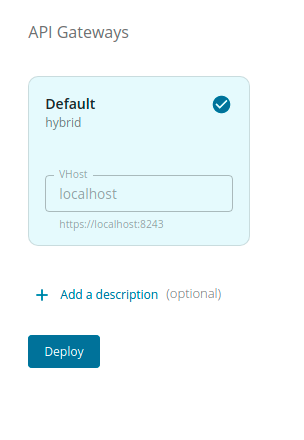
-
Click Deploy.
-
Go to Overview using the left menu pane.

-
Click Publish.

-
The deployed DCR API is now available in the Developer Portal at
https://<APIM_HOST>:9443/devportal. -
Upload the root and issuer certificates in OBIE (Sandbox certificates/ Production certificates) to the client trust stores in
<APIM_HOME>/repository/resources/security/client-truststore.jksand<IS_HOME>/repository/resources/security/client-truststore.jksusing the following command:keytool -import -alias <alias> -file <certificate_location> -storetype JKS -keystore <truststore_location> -storepass wso2carbon -
Restart the Identity Server and API Manager instances.
Step 2: Configure IS as Key Manager¶
- Sign in to the Admin Portal of API Manager at
https://<APIM_HOST>:9443/admin. - Go to Key Manager on the left main menu.
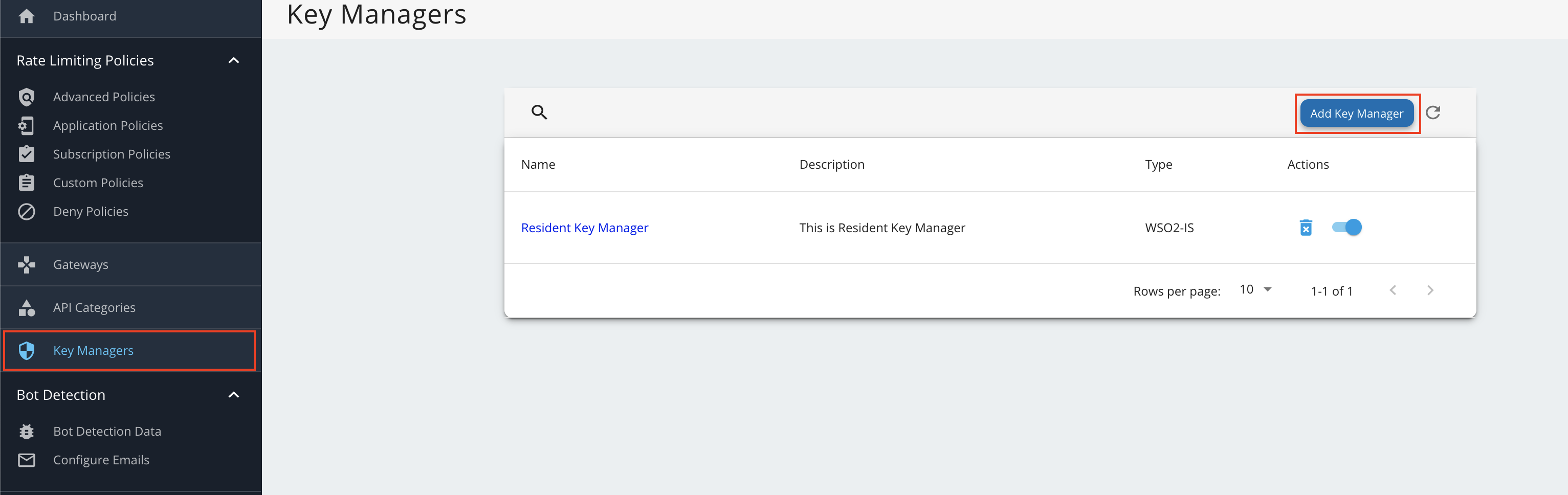
-
Click Add New Key Manager and configure Key Manager.
Click here to see the full list of configurations...
Configuration Description Value Name The name of the authorization server. OBKM Display Name A name to display on the UI. OBKM Description The name of the authorization server. (Optional) Key Manager Type The type of the Key Manager to be selected. Select ObKeyManagerWell-known-url The well-known URL of the authorization server (Key Manager). https://<IS_HOST>:9446/oauth2/token/.well-known/openid-configurationIssuer The issuer that consumes or validates access tokens. https://<IS_HOST>:9446/oauth2/tokenKey Manager Endpoints Client Registration Endpoint The endpoint that verifies the identity and obtain profile information of the end-user based on the authentication performed by an authorization server. https://<IS_HOST>:9446/keymanager-operations/dcr/registerIntrospection Endpoint The endpoint that allows authorized protected resources to query the authorization server to determine the set of metadata for a given token that was presented to them by an OAuth Client. https://<IS_HOST>:9446/oauth2/introspectToken Endpoint The endpoint that issues the access tokens. https://<IS_HOST>:9446/oauth2/tokenRevoke Endpoint The endpoint that revokes the access tokens. https://<IS_HOST>:9446/oauth2/revokeUserinfo Endpoint The endpoint that allows clients to verify the identity of the end-user based on the authentication performed by an authorization server, as well as to obtain basic profile information about the end-user. https://<IS_HOST>:9446/oauth2/userinfo?schema=openidAuthorize Endpoint The endpoint used to obtain an authorization grant from the resource owner via the user-agent redirection. https://<IS_HOST>:9446/oauth2/authorizeScope Management Endpoint The endpoint used to manage the scopes. https://<IS_HOST>:9446/api/identity/oauth2/v1.0/scopesConnector Configurations Username The username of an admin user who is authorized to connect to the authorization server. Password The password corresponding to the latter mentioned admin user who is authorized to connect to the authorization server. Claim URIs Consumer Key Claim URI The claim URI for the consumer key. (Optional) Scopes Claim URI The claim URI for the scopes (Optional) Grant Types The supported grant types. Add multiple grant types by adding a grant type press Enter. Add the client_credentials,authorization_code,refresh_token, andurn:ietf:params:oauth:grant-type:jwt-bearergrant types.(Mandatory) Certificates PEM Either copy and paste the certificate in PEM format or upload the PEM file. (Optional) JWKS The JSON Web Key Set (JWKS) endpoint is a read-only endpoint. This URL returns the Identity Server's public key set in JSON web key set format. This contains the signing key(s) the Relying Party (RP) uses to validate signatures from the Identity Server. https://<IS_HOST>:9446/oauth2/jwksAdvanced Configurations Token Generation This enables token generation via the authorization server. (Mandatory) Out Of Band Provisioning This enables the provisioning of Auth clients that have been created without the use of the Developer Portal, such as previously created Auth clients. (Mandatory) Oauth App Creation This enables the creation of Auth clients. (Mandatory) Token Validation Method The method used to validate the JWT signature. Self Validate JWT The kid value is used to validate the JWT token signature. If the kid value is not present, gateway_certificate_aliaswill be used.(Mandatory) Use introspect The JWKS endpoint is used to validate the JWT token signature. - Token Handling Options This provides a way to validate the token for this particular authorization server. This is mandatory if the Token Validation Method is introspect. (Optional) REFERENCE The tokens that match a specific regular expression (regEx) are validated. e.g., [0-9a-fA-F]{8}-[0-9a-fA-F]{4}-[1-5][0-9a-fA-F]{3}-[89abAB][0-9a-fA-F]{3}-[0-9a-fA-F]{12}(Optional) JWT The tokens that match a specific JWT are validated. Select this icon CUSTOM The tokens that match a custom pattern are validated. (Optional) Claim Mappings Local and remote claim mapping. (Optional) -
Go to the list of Key Managers and select Resident Key Manager.
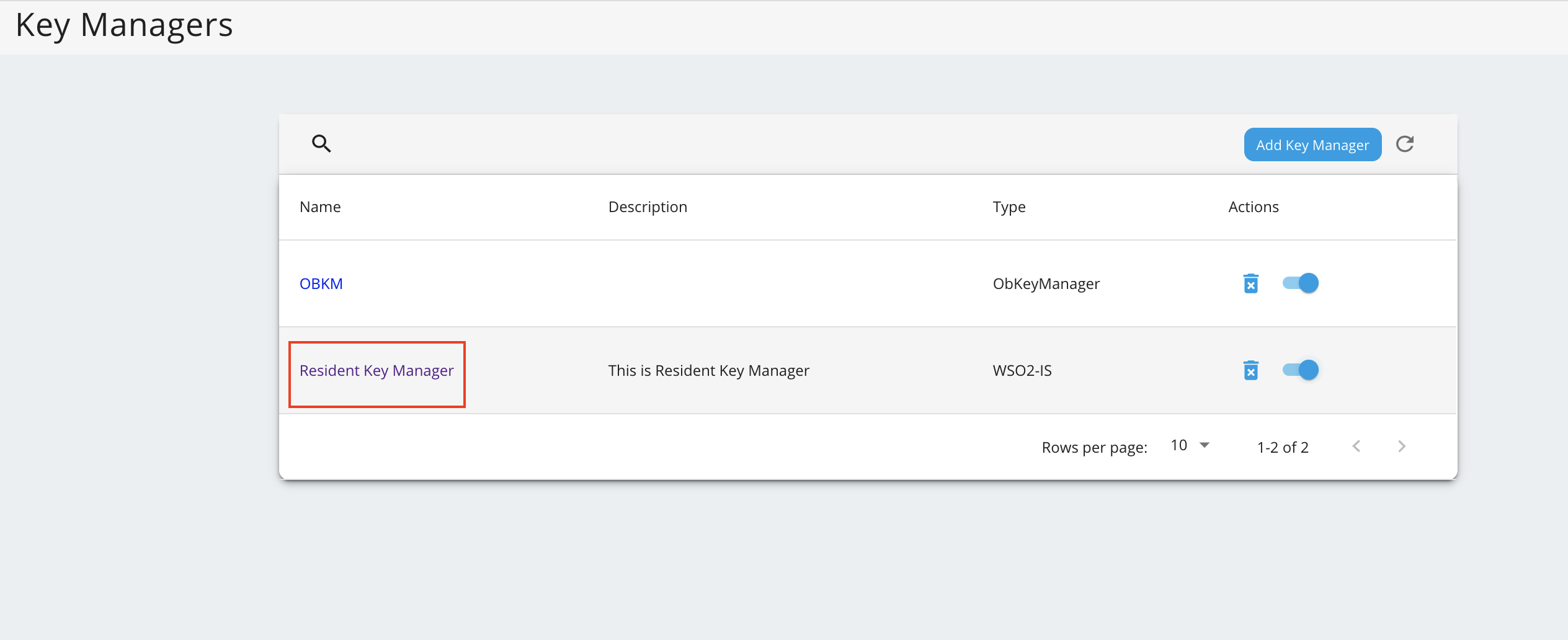
-
Locate Connector Configurations and provide a username and a password for a user with super admin credentials.
-
Click Update.
-
Disable the Resident Key Manager.
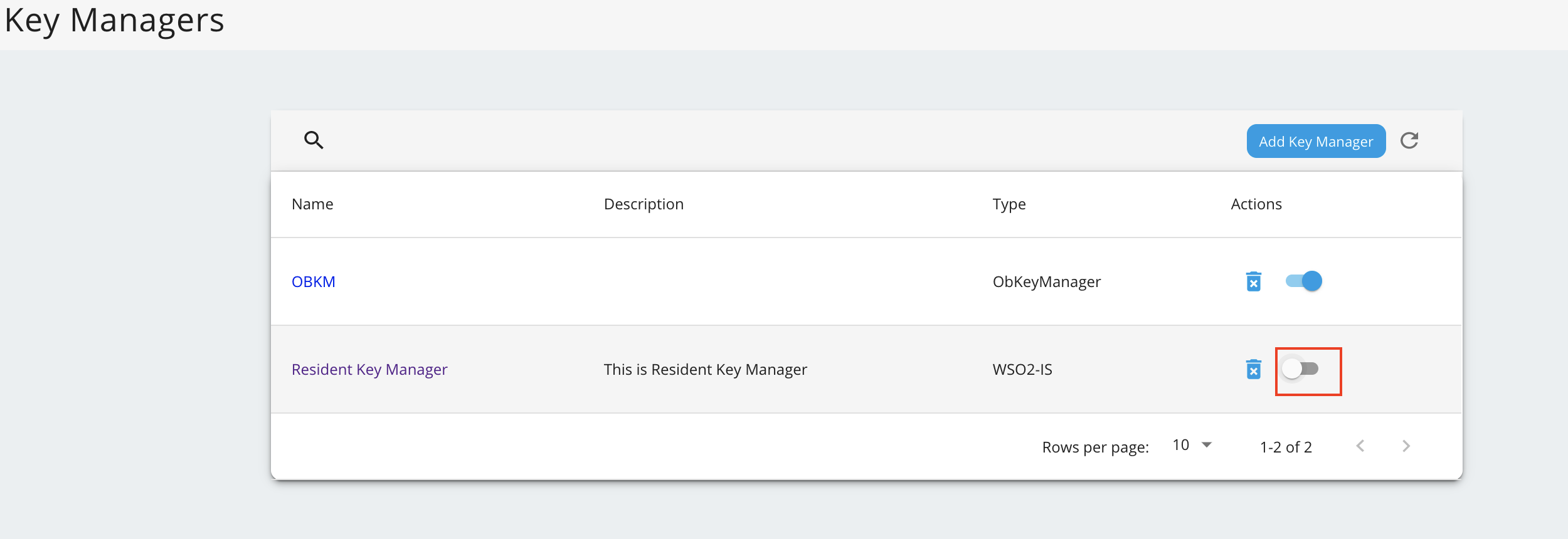
Note
If you are using an API Manager at U2 level 4.0.0.102 or above, make sure the Resident Key Manager configurations are disabled. For more information, see Configuring DCR in API Manager - Step 10.
Step 3: Tryout DCR¶
Tip
If you have Postman, import the script to invoke the DCR endpoints for the scenarios explained below.
Register an application¶
The API allows the API consumer to request the bank to register a new application. The process is as follows:
- The API consumer sends a registration request including a Software Statement Assertion (SSA) as a claim in the payload. This SSA contains API consumer's metadata. A sample request looks as follows:
For Transport Layer Security purposes in this sample flow, you can use the attached private key and public certificate.
curl -X POST https://<APIM_HOST>:8243/open-banking/0.1/register \
-H 'Content-Type: application/jwt' \
--cert <TRANSPORT_PUBLIC_CERT_FILE_PATH> --key <TRANSPORT_PRIVATE_KEY_FILE_PATH> \
-d 'eyJ0eXAiOiJKV1QiLCJhbGciOiJQUzI1NiIsImtpZCI6Inc3TkZlTU9EekNNT1plbl9XRUNBbEc5TjhnZyJ9.eyJpc3MiOiJvUTRLb2FhdnBPdW9FN3J2UXNaRU9WMyIsImlhdCI6MTU3MTgwODE2NywiZXhwIjoyMTQ3NDgzNjQ2LCJqdGkiOiIzNzc0N2NkMWMxMDU0NTY5OWY3NTRhZGYyOGI3M2UzMiIsImF1ZCI6Imh0dHBzOi8vc2VjdXJlLmFwaS5kYXRhaG9sZGVyLmNvbS9pc3N1ZXIiLCJyZWRpcmVjdF91cmlzIjpbImh0dHBzOi8vd3d3Lm1vY2tjb21wYW55LmNvbS9yZWRpcmVjdHMvcmVkaXJlY3QxIl0sInRva2VuX2VuZHBvaW50X2F1dGhfc2lnbmluZ19hbGciOiJQUzI1NiIsInRva2VuX2VuZHBvaW50X2F1dGhfbWV0aG9kIjoicHJpdmF0ZV9rZXlfand0IiwiZ3JhbnRfdHlwZXMiOlsiY2xpZW50X2NyZWRlbnRpYWxzIiwiYXV0aG9yaXphdGlvbl9jb2RlIiwicmVmcmVzaF90b2tlbiIsInVybjppZXRmOnBhcmFtczpvYXV0aDpncmFudC10eXBlOmp3dC1iZWFyZXIiXSwicmVzcG9uc2VfdHlwZXMiOlsiY29kZSBpZF90b2tlbiJdLCJhcHBsaWNhdGlvbl90eXBlIjoid2ViIiwiaWRfdG9rZW5fc2lnbmVkX3Jlc3BvbnNlX2FsZyI6IlBTMjU2IiwiaWRfdG9rZW5fZW5jcnlwdGVkX3Jlc3BvbnNlX2FsZyI6IlJTQS1PQUVQIiwiaWRfdG9rZW5fZW5jcnlwdGVkX3Jlc3BvbnNlX2VuYyI6IkEyNTZHQ00iLCJyZXF1ZXN0X29iamVjdF9zaWduaW5nX2FsZyI6IlBTMjU2Iiwic2NvcGUiOiJvcGVuaWQgYWNjb3VudHMgcGF5bWVudHMiLCJzb2Z0d2FyZV9zdGF0ZW1lbnQiOiJleUpoYkdjaU9pSlFVekkxTmlJc0ltdHBaQ0k2SW5jM1RrWmxUVTlFZWtOTlQxcGxibDlYUlVOQmJFYzVUamhuWnlJc0luUjVjQ0k2SWtwWFZDSjkuZXlKcGMzTWlPaUpQY0dWdVFtRnVhMmx1WnlCTWRHUWlMQ0pwWVhRaU9qRTJORGMwTURVNU5EQXNJbXAwYVNJNklqTTJZalZrWm1Vd01qQTFZelF3TmpBaUxDSnpiMlowZDJGeVpWOWxiblpwY205dWJXVnVkQ0k2SW5OaGJtUmliM2dpTENKemIyWjBkMkZ5WlY5dGIyUmxJam9pVkdWemRDSXNJbk52Wm5SM1lYSmxYMmxrSWpvaWIxRTBTMjloWVhad1QzVnZSVGR5ZGxGeldrVlBWak1pTENKemIyWjBkMkZ5WlY5amJHbGxiblJmYVdRaU9pSnZVVFJMYjJGaGRuQlBkVzlGTjNKMlVYTmFSVTlXTXlJc0luTnZablIzWVhKbFgyTnNhV1Z1ZEY5dVlXMWxJam9pVjFOUE1pQlBjR1Z1SUVKaGJtdHBibWNnVkZCUU1pQW9VMkZ1WkdKdmVDa2lMQ0p6YjJaMGQyRnlaVjlqYkdsbGJuUmZaR1Z6WTNKcGNIUnBiMjRpT2lKWFUwOHlJRTl3Wlc0Z1FtRnVhMmx1WnlCVVVGQXlJR1p2Y2lCMFpYTjBhVzVuSWl3aWMyOW1kSGRoY21WZmRtVnljMmx2YmlJNk1TNDFMQ0p6YjJaMGQyRnlaVjlqYkdsbGJuUmZkWEpwSWpvaWFIUjBjSE02THk5M2QzY3ViVzlqYTJOdmJYQmhibmt1WTI5dEwzSmxaR2x5WldOMGN5OXlaV1JwY21WamRERWlMQ0p6YjJaMGQyRnlaVjl5WldScGNtVmpkRjkxY21seklqcGJJbWgwZEhCek9pOHZkM2QzTG0xdlkydGpiMjF3WVc1NUxtTnZiUzl5WldScGNtVmpkSE12Y21Wa2FYSmxZM1F4SWwwc0luTnZablIzWVhKbFgzSnZiR1Z6SWpwYklsQkpVMUFpTENKQlNWTlFJaXdpUTBKUVNVa2lYU3dpYjNKbllXNXBjMkYwYVc5dVgyTnZiWEJsZEdWdWRGOWhkWFJvYjNKcGRIbGZZMnhoYVcxeklqcDdJbUYxZEdodmNtbDBlVjlwWkNJNklrOUNSMEpTSWl3aWNtVm5hWE4wY21GMGFXOXVYMmxrSWpvaVZXNXJibTkzYmpBd01UVTRNREF3TURGSVVWRnlXa0ZCV0NJc0luTjBZWFIxY3lJNklrRmpkR2wyWlNJc0ltRjFkR2h2Y21sellYUnBiMjV6SWpwYmV5SnRaVzFpWlhKZmMzUmhkR1VpT2lKSFFpSXNJbkp2YkdWeklqcGJJbEJKVTFBaUxDSkJTVk5RSWl3aVEwSlFTVWtpWFgwc2V5SnRaVzFpWlhKZmMzUmhkR1VpT2lKSlJTSXNJbkp2YkdWeklqcGJJbEJKVTFBaUxDSkRRbEJKU1NJc0lrRkpVMUFpWFgwc2V5SnRaVzFpWlhKZmMzUmhkR1VpT2lKT1RDSXNJbkp2YkdWeklqcGJJbEJKVTFBaUxDSkJTVk5RSWl3aVEwSlFTVWtpWFgxZGZTd2ljMjltZEhkaGNtVmZiRzluYjE5MWNta2lPaUpvZEhSd2N6b3ZMM2R6YnpJdVkyOXRMM2R6YnpJdWFuQm5JaXdpYjNKblgzTjBZWFIxY3lJNklrRmpkR2wyWlNJc0ltOXlaMTlwWkNJNklqQXdNVFU0TURBd01ERklVVkZ5V2tGQldDSXNJbTl5WjE5dVlXMWxJam9pVjFOUE1pQW9WVXNwSUV4SlRVbFVSVVFpTENKdmNtZGZZMjl1ZEdGamRITWlPbHQ3SW01aGJXVWlPaUpVWldOb2JtbGpZV3dpTENKbGJXRnBiQ0k2SW5SbGMzUkFkM052TWk1amIyMGlMQ0p3YUc5dVpTSTZJaXM1TkRBd01EQXdNREF3TUNJc0luUjVjR1VpT2lKVVpXTm9ibWxqWVd3aWZTeDdJbTVoYldVaU9pSkNkWE5wYm1WemN5SXNJbVZ0WVdsc0lqb2lkR1Z6ZEVCM2MyOHlMbU52YlNJc0luQm9iMjVsSWpvaUt6azBNREF3TURBd01EQXdJaXdpZEhsd1pTSTZJa0oxYzJsdVpYTnpJbjFkTENKdmNtZGZhbmRyYzE5bGJtUndiMmx1ZENJNkltaDBkSEJ6T2k4dmEyVjVjM1J2Y21VdWIzQmxibUpoYm10cGJtZDBaWE4wTG05eVp5NTFheTh3TURFMU9EQXdNREF4U0ZGUmNscEJRVmd2TURBeE5UZ3dNREF3TVVoUlVYSmFRVUZZTG1wM2EzTWlMQ0p2Y21kZmFuZHJjMTl5WlhadmEyVmtYMlZ1WkhCdmFXNTBJam9pYUhSMGNITTZMeTlyWlhsemRHOXlaUzV2Y0dWdVltRnVhMmx1WjNSbGMzUXViM0puTG5Wckx6QXdNVFU0TURBd01ERklVVkZ5V2tGQldDOXlaWFp2YTJWa0x6QXdNVFU0TURBd01ERklVVkZ5V2tGQldDNXFkMnR6SWl3aWMyOW1kSGRoY21WZmFuZHJjMTlsYm1Sd2IybHVkQ0k2SW1oMGRIQnpPaTh2YTJWNWMzUnZjbVV1YjNCbGJtSmhibXRwYm1kMFpYTjBMbTl5Wnk1MWF5OHdNREUxT0RBd01EQXhTRkZSY2xwQlFWZ3ZiMUUwUzI5aFlYWndUM1Z2UlRkeWRsRnpXa1ZQVmk1cWQydHpJaXdpYzI5bWRIZGhjbVZmYW5kcmMxOXlaWFp2YTJWa1gyVnVaSEJ2YVc1MElqb2lhSFIwY0hNNkx5OXJaWGx6ZEc5eVpTNXZjR1Z1WW1GdWEybHVaM1JsYzNRdWIzSm5MblZyTHpBd01UVTRNREF3TURGSVVWRnlXa0ZCV0M5eVpYWnZhMlZrTDI5Uk5FdHZZV0YyY0U5MWIwVTNjblpSYzFwRlQxWXVhbmRyY3lJc0luTnZablIzWVhKbFgzQnZiR2xqZVY5MWNta2lPaUpvZEhSd2N6b3ZMM2R6YnpJdVkyOXRJaXdpYzI5bWRIZGhjbVZmZEc5elgzVnlhU0k2SW1oMGRIQnpPaTh2ZDNOdk1pNWpiMjBpTENKemIyWjBkMkZ5WlY5dmJsOWlaV2hoYkdaZmIyWmZiM0puSWpvaVYxTlBNaUJQY0dWdUlFSmhibXRwYm1jaWZRLldRNTdCaFRtYjZqdWtFN0JZRHFoMjRkUDZkTXVSdWUxbEpaZ2VJWHVGY0RLbE5aN2tGX1lvaWZpMktwSXhxQmxLN1poc2N1YVRYam0tcG9NVEpFTHpBV2luN1dza1hJR0UwZVJuQldVUi1lZnlEZHgtbTdEWDNWU003WlJfeVhDV3lIOUFKWXlwdTFtMjJrWHowU2lYOHFkWERFY0F5Z0R1RGdaTThJWWJwS1pURlhfdWlLaXNyM2tWQm04SmRSZDkyT3JWUzVhQ096YzdWVnpVTW04Uk5OOTQwdkFVYW5zS3JKMlgxSk9heUoyVVRCNnJTdlJta3o1a013S1lzeHBvaGNoenlmQ3BRME1CTFRGU2VnZGprU3lsQTlheGVnZ1VzVUNDYzlUcmx5X1BoanZXVURURW9LcUFvYm1FbGlZWV9xLUs1RFBUdFU3cDNBcXBzLUFwZyJ9.LtQWYCXqXhGQR43WpOX5f2FpGGjku2SLdgUwGu83qRSUiBsyVuhQBVs7ABOA8hIracQZbxgbnl1VRgJ_Nsr8OwcjbJfFP1lnGkRREytaIsWkTHe_8p6RZdfjev2TxvyJbfWtZTr5JT6OsuuA4LLvRN09bYjfPTYp1cOTuiTpLyVoEN4B5fTrAExknwivDygdgf2fZHj_u5TClbPCGkwIZrY6dNaaDK2vxzYKztfH-g9RgDixmX_GY3jdU4jPh434oGu18cRVP6dMqEQ-Jo-H43GE2mFGQIh3k819J17ImauVC55ty-owkLHs23Rxjn4R8_-DCG3uEdvz-63EY_KxeQ' The payload is a signed JWT.
Click here to see the decoded format of the payload...
{
"typ": "JWT",
"alg": "PS256",
"kid": "w7NFeMODzCMOZen_WECAlG9N8gg"
}
{
"iss": "oQ4KoaavpOuoE7rvQsZEOV3",
"iat": 1571808167,
"exp": 2147483646,
"jti": "37747cd1c10545699f754adf28b73e31",
"aud": "https://secure.api.dataholder.com/issuer",
"redirect_uris": [
"https://www.mockcompany.com/redirects/redirect1"
],
"token_endpoint_auth_signing_alg": "PS256",
"token_endpoint_auth_method": "private_key_jwt",
"grant_types": [
"client_credentials",
"authorization_code",
"refresh_token",
"urn:ietf:params:oauth:grant-type:jwt-bearer"
],
"response_types": [
"code id_token"
],
"application_type": "web",
"id_token_signed_response_alg": "PS256",
"id_token_encrypted_response_alg": "RSA-OAEP",
"id_token_encrypted_response_enc": "A256GCM",
"request_object_signing_alg": "PS256",
"scope": "openid accounts payments",
"software_statement": "eyJhbGciOiJQUzI1NiIsImtpZCI6Inc3TkZlTU9EekNNT1plbl9XRUNBbEc5TjhnZyIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJPcGVuQmFua2luZyBMdGQiLCJpYXQiOjE2NDc0MDU5NDAsImp0aSI6IjM2YjVkZmUwMjA1YzQwNjAiLCJzb2Z0d2FyZV9lbnZpcm9ubWVudCI6InNhbmRib3giLCJzb2Z0d2FyZV9tb2RlIjoiVGVzdCIsInNvZnR3YXJlX2lkIjoib1E0S29hYXZwT3VvRTdydlFzWkVPVjMiLCJzb2Z0d2FyZV9jbGllbnRfaWQiOiJvUTRLb2FhdnBPdW9FN3J2UXNaRU9WMyIsInNvZnR3YXJlX2NsaWVudF9uYW1lIjoiV1NPMiBPcGVuIEJhbmtpbmcgVFBQMiAoU2FuZGJveCkiLCJzb2Z0d2FyZV9jbGllbnRfZGVzY3JpcHRpb24iOiJXU08yIE9wZW4gQmFua2luZyBUUFAyIGZvciB0ZXN0aW5nIiwic29mdHdhcmVfdmVyc2lvbiI6MS41LCJzb2Z0d2FyZV9jbGllbnRfdXJpIjoiaHR0cHM6Ly93d3cubW9ja2NvbXBhbnkuY29tL3JlZGlyZWN0cy9yZWRpcmVjdDEiLCJzb2Z0d2FyZV9yZWRpcmVjdF91cmlzIjpbImh0dHBzOi8vd3d3Lm1vY2tjb21wYW55LmNvbS9yZWRpcmVjdHMvcmVkaXJlY3QxIl0sInNvZnR3YXJlX3JvbGVzIjpbIlBJU1AiLCJBSVNQIiwiQ0JQSUkiXSwib3JnYW5pc2F0aW9uX2NvbXBldGVudF9hdXRob3JpdHlfY2xhaW1zIjp7ImF1dGhvcml0eV9pZCI6Ik9CR0JSIiwicmVnaXN0cmF0aW9uX2lkIjoiVW5rbm93bjAwMTU4MDAwMDFIUVFyWkFBWCIsInN0YXR1cyI6IkFjdGl2ZSIsImF1dGhvcmlzYXRpb25zIjpbeyJtZW1iZXJfc3RhdGUiOiJHQiIsInJvbGVzIjpbIlBJU1AiLCJBSVNQIiwiQ0JQSUkiXX0seyJtZW1iZXJfc3RhdGUiOiJJRSIsInJvbGVzIjpbIlBJU1AiLCJDQlBJSSIsIkFJU1AiXX0seyJtZW1iZXJfc3RhdGUiOiJOTCIsInJvbGVzIjpbIlBJU1AiLCJBSVNQIiwiQ0JQSUkiXX1dfSwic29mdHdhcmVfbG9nb191cmkiOiJodHRwczovL3dzbzIuY29tL3dzbzIuanBnIiwib3JnX3N0YXR1cyI6IkFjdGl2ZSIsIm9yZ19pZCI6IjAwMTU4MDAwMDFIUVFyWkFBWCIsIm9yZ19uYW1lIjoiV1NPMiAoVUspIExJTUlURUQiLCJvcmdfY29udGFjdHMiOlt7Im5hbWUiOiJUZWNobmljYWwiLCJlbWFpbCI6InRlc3RAd3NvMi5jb20iLCJwaG9uZSI6Iis5NDAwMDAwMDAwMCIsInR5cGUiOiJUZWNobmljYWwifSx7Im5hbWUiOiJCdXNpbmVzcyIsImVtYWlsIjoidGVzdEB3c28yLmNvbSIsInBob25lIjoiKzk0MDAwMDAwMDAwIiwidHlwZSI6IkJ1c2luZXNzIn1dLCJvcmdfandrc19lbmRwb2ludCI6Imh0dHBzOi8va2V5c3RvcmUub3BlbmJhbmtpbmd0ZXN0Lm9yZy51ay8wMDE1ODAwMDAxSFFRclpBQVgvMDAxNTgwMDAwMUhRUXJaQUFYLmp3a3MiLCJvcmdfandrc19yZXZva2VkX2VuZHBvaW50IjoiaHR0cHM6Ly9rZXlzdG9yZS5vcGVuYmFua2luZ3Rlc3Qub3JnLnVrLzAwMTU4MDAwMDFIUVFyWkFBWC9yZXZva2VkLzAwMTU4MDAwMDFIUVFyWkFBWC5qd2tzIiwic29mdHdhcmVfandrc19lbmRwb2ludCI6Imh0dHBzOi8va2V5c3RvcmUub3BlbmJhbmtpbmd0ZXN0Lm9yZy51ay8wMDE1ODAwMDAxSFFRclpBQVgvb1E0S29hYXZwT3VvRTdydlFzWkVPVi5qd2tzIiwic29mdHdhcmVfandrc19yZXZva2VkX2VuZHBvaW50IjoiaHR0cHM6Ly9rZXlzdG9yZS5vcGVuYmFua2luZ3Rlc3Qub3JnLnVrLzAwMTU4MDAwMDFIUVFyWkFBWC9yZXZva2VkL29RNEtvYWF2cE91b0U3cnZRc1pFT1YuandrcyIsInNvZnR3YXJlX3BvbGljeV91cmkiOiJodHRwczovL3dzbzIuY29tIiwic29mdHdhcmVfdG9zX3VyaSI6Imh0dHBzOi8vd3NvMi5jb20iLCJzb2Z0d2FyZV9vbl9iZWhhbGZfb2Zfb3JnIjoiV1NPMiBPcGVuIEJhbmtpbmcifQ.WQ57BhTmb6jukE7BYDqh24dP6dMuRue1lJZgeIXuFcDKlNZ7kF_Yoifi2KpIxqBlK7ZhscuaTXjm-poMTJELzAWin7WskXIGE0eRnBWUR-efyDdx-m7DX3VSM7ZR_yXCWyH9AJYypu1m22kXz0SiX8qdXDEcAygDuDgZM8IYbpKZTFX_uiKisr3kVBm8JdRd92OrVS5aCOzc7VVzUMm8RNN940vAUansKrJ2X1JOayJ2UTB6rSvRmkz5kMwKYsxpohchzyfCpQ0MBLTFSegdjkSylA9axeggUsUCCc9Trly_PhjvWUDTEoKqAobmEliYY_q-K5DPTtU7p3Aqps-Apg"
}
<signature>Click here to see the decoded format of an SSA...
{
"alg": "PS256",
"kid": "w7NFeMODzCMOZen_WECAlG9N8gg",
"typ": "JWT"
}
{
"iss": "OpenBanking Ltd",
"iat": 1647405940,
"jti": "36b5dfe0205c4060",
"software_environment": "sandbox",
"software_mode": "Test",
"software_id": "oQ4KoaavpOuoE7rvQsZEOV3",
"software_client_id": "oQ4KoaavpOuoE7rvQsZEOV3",
"software_client_name": "WSO2 Open Banking TPP2 (Sandbox)",
"software_client_description": "WSO2 Open Banking TPP2 for testing",
"software_version": 1.5,
"software_client_uri": "https://www.mockcompany.com/redirects/redirect1",
"software_redirect_uris": [
"https://www.mockcompany.com/redirects/redirect1"
],
"software_roles": [
"PISP",
"AISP",
"CBPII"
],
"organisation_competent_authority_claims": {
"authority_id": "OBGBR",
"registration_id": "Unknown0015800001HQQrZAAX",
"status": "Active",
"authorisations": [
{
"member_state": "GB",
"roles": [
"PISP",
"AISP",
"CBPII"
]
},
{
"member_state": "IE",
"roles": [
"PISP",
"CBPII",
"AISP"
]
},
{
"member_state": "NL",
"roles": [
"PISP",
"AISP",
"CBPII"
]
}
]
},
"software_logo_uri": "https://wso2.com/wso2.jpg",
"org_status": "Active",
"org_id": "0015800001HQQrZAAX",
"org_name": "WSO2 (UK) LIMITED",
"org_contacts": [
{
"name": "Technical",
"email": "[email protected]",
"phone": "+94000000000",
"type": "Technical"
},
{
"name": "Business",
"email": "[email protected]",
"phone": "+94000000000",
"type": "Business"
}
],
"org_jwks_endpoint": "https://keystore.openbankingtest.org.uk/0015800001HQQrZAAX/0015800001HQQrZAAX.jwks",
"org_jwks_revoked_endpoint": "https://keystore.openbankingtest.org.uk/0015800001HQQrZAAX/revoked/0015800001HQQrZAAX.jwks",
"software_jwks_endpoint": "https://keystore.openbankingtest.org.uk/0015800001HQQrZAAX/oQ4KoaavpOuoE7rvQsZEOV.jwks",
"software_jwks_revoked_endpoint": "https://keystore.openbankingtest.org.uk/0015800001HQQrZAAX/revoked/oQ4KoaavpOuoE7rvQsZEOV.jwks",
"software_policy_uri": "https://wso2.com",
"software_tos_uri": "https://wso2.com",
"software_on_behalf_of_org": "WSO2 Open Banking"
}
<signature>Note
If you change the payload, use the following certificates to sign the JWT and SSA:
-
The bank registers the application using the metadata sent in the SSA.
-
If an application is successfully created, the bank responds with a JSON payload describing the API consumer that the application was created. The API consumer can then use the identifier (
CONSUMER_KEY) to access customers' financial data on the bank's resource server. A sample response is given below:{ "client_id":"ZRsNz6FOaNSWjEwEGFW_Osid8aAa", "client_id_issued_at":"1664173296", "redirect_uris":[ "https://www.mockcompany.com/redirects/redirect1" ], "grant_types":[ "client_credentials", "authorization_code", "refresh_token", "urn:ietf:params:oauth:grant-type:jwt-bearer" ], "response_types":[ "code id_token" ], "application_type":"web", "id_token_signed_response_alg":"PS256", "request_object_signing_alg":"PS256", "scope":"openid accounts payments", "software_id":"oQ4KoaavpOuoE7rvQsZEOV3", "token_endpoint_auth_method":"private_key_jwt", "software_statement":"eyJhbGciOiJQUzI1NiIsImtpZCI6Inc3TkZlTU9EekNNT1plbl9XRUNBbEc5TjhnZyIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJPcGVuQmFua2luZyBMdGQiLCJpYXQiOjE2NDc0MDU5NDAsImp0aSI6IjM2YjVkZmUwMjA1YzQwNjAiLCJzb2Z0d2FyZV9lbnZpcm9ubWVudCI6InNhbmRib3giLCJzb2Z0d2FyZV9tb2RlIjoiVGVzdCIsInNvZnR3YXJlX2lkIjoib1E0S29hYXZwT3VvRTdydlFzWkVPVjMiLCJzb2Z0d2FyZV9jbGllbnRfaWQiOiJvUTRLb2FhdnBPdW9FN3J2UXNaRU9WMyIsInNvZnR3YXJlX2NsaWVudF9uYW1lIjoiV1NPMiBPcGVuIEJhbmtpbmcgVFBQMiAoU2FuZGJveCkiLCJzb2Z0d2FyZV9jbGllbnRfZGVzY3JpcHRpb24iOiJXU08yIE9wZW4gQmFua2luZyBUUFAyIGZvciB0ZXN0aW5nIiwic29mdHdhcmVfdmVyc2lvbiI6MS41LCJzb2Z0d2FyZV9jbGllbnRfdXJpIjoiaHR0cHM6Ly93d3cubW9ja2NvbXBhbnkuY29tL3JlZGlyZWN0cy9yZWRpcmVjdDEiLCJzb2Z0d2FyZV9yZWRpcmVjdF91cmlzIjpbImh0dHBzOi8vd3d3Lm1vY2tjb21wYW55LmNvbS9yZWRpcmVjdHMvcmVkaXJlY3QxIl0sInNvZnR3YXJlX3JvbGVzIjpbIlBJU1AiLCJBSVNQIiwiQ0JQSUkiXSwib3JnYW5pc2F0aW9uX2NvbXBldGVudF9hdXRob3JpdHlfY2xhaW1zIjp7ImF1dGhvcml0eV9pZCI6Ik9CR0JSIiwicmVnaXN0cmF0aW9uX2lkIjoiVW5rbm93bjAwMTU4MDAwMDFIUVFyWkFBWCIsInN0YXR1cyI6IkFjdGl2ZSIsImF1dGhvcmlzYXRpb25zIjpbeyJtZW1iZXJfc3RhdGUiOiJHQiIsInJvbGVzIjpbIlBJU1AiLCJBSVNQIiwiQ0JQSUkiXX0seyJtZW1iZXJfc3RhdGUiOiJJRSIsInJvbGVzIjpbIlBJU1AiLCJDQlBJSSIsIkFJU1AiXX0seyJtZW1iZXJfc3RhdGUiOiJOTCIsInJvbGVzIjpbIlBJU1AiLCJBSVNQIiwiQ0JQSUkiXX1dfSwic29mdHdhcmVfbG9nb191cmkiOiJodHRwczovL3dzbzIuY29tL3dzbzIuanBnIiwib3JnX3N0YXR1cyI6IkFjdGl2ZSIsIm9yZ19pZCI6IjAwMTU4MDAwMDFIUVFyWkFBWCIsIm9yZ19uYW1lIjoiV1NPMiAoVUspIExJTUlURUQiLCJvcmdfY29udGFjdHMiOlt7Im5hbWUiOiJUZWNobmljYWwiLCJlbWFpbCI6InRlc3RAd3NvMi5jb20iLCJwaG9uZSI6Iis5NDAwMDAwMDAwMCIsInR5cGUiOiJUZWNobmljYWwifSx7Im5hbWUiOiJCdXNpbmVzcyIsImVtYWlsIjoidGVzdEB3c28yLmNvbSIsInBob25lIjoiKzk0MDAwMDAwMDAwIiwidHlwZSI6IkJ1c2luZXNzIn1dLCJvcmdfandrc19lbmRwb2ludCI6Imh0dHBzOi8va2V5c3RvcmUub3BlbmJhbmtpbmd0ZXN0Lm9yZy51ay8wMDE1ODAwMDAxSFFRclpBQVgvMDAxNTgwMDAwMUhRUXJaQUFYLmp3a3MiLCJvcmdfandrc19yZXZva2VkX2VuZHBvaW50IjoiaHR0cHM6Ly9rZXlzdG9yZS5vcGVuYmFua2luZ3Rlc3Qub3JnLnVrLzAwMTU4MDAwMDFIUVFyWkFBWC9yZXZva2VkLzAwMTU4MDAwMDFIUVFyWkFBWC5qd2tzIiwic29mdHdhcmVfandrc19lbmRwb2ludCI6Imh0dHBzOi8va2V5c3RvcmUub3BlbmJhbmtpbmd0ZXN0Lm9yZy51ay8wMDE1ODAwMDAxSFFRclpBQVgvb1E0S29hYXZwT3VvRTdydlFzWkVPVi5qd2tzIiwic29mdHdhcmVfandrc19yZXZva2VkX2VuZHBvaW50IjoiaHR0cHM6Ly9rZXlzdG9yZS5vcGVuYmFua2luZ3Rlc3Qub3JnLnVrLzAwMTU4MDAwMDFIUVFyWkFBWC9yZXZva2VkL29RNEtvYWF2cE91b0U3cnZRc1pFT1YuandrcyIsInNvZnR3YXJlX3BvbGljeV91cmkiOiJodHRwczovL3dzbzIuY29tIiwic29mdHdhcmVfdG9zX3VyaSI6Imh0dHBzOi8vd3NvMi5jb20iLCJzb2Z0d2FyZV9vbl9iZWhhbGZfb2Zfb3JnIjoiV1NPMiBPcGVuIEJhbmtpbmcifQ.WQ57BhTmb6jukE7BYDqh24dP6dMuRue1lJZgeIXuFcDKlNZ7kF_Yoifi2KpIxqBlK7ZhscuaTXjm-poMTJELzAWin7WskXIGE0eRnBWUR-efyDdx-m7DX3VSM7ZR_yXCWyH9AJYypu1m22kXz0SiX8qdXDEcAygDuDgZM8IYbpKZTFX_uiKisr3kVBm8JdRd92OrVS5aCOzc7VVzUMm8RNN940vAUansKrJ2X1JOayJ2UTB6rSvRmkz5kMwKYsxpohchzyfCpQ0MBLTFSegdjkSylA9axeggUsUCCc9Trly_PhjvWUDTEoKqAobmEliYY_q-K5DPTtU7p3Aqps-Apg" } -
If application creation is unsuccessful, the bank responds with an error payload.
Generate an application access token using Client Credentials grant. A sample command is given below.
curl -X POST https://<IS_HOST>:9446/oauth2/token \
-H 'Content-Type: application/x-www-form-urlencoded' \
--cert <TRANSPORT_PUBLIC_KEY_FILE_PATH> --key <TRANSPORT_PRIVATE_KEY_FILE_PATH> \
-d 'grant_type=client_credentials&scope=accountsopenid&client_assertion=<CLIENT_ASSERTION>&client_assertion_type=urn:ietf:params:oauth:client-assertion-type:jwt-bearer&redirect_uri=<REDIRECT_URI>&client_id=<CONSUMER_KEY>’Make sure to update the placeholders with the relevant values
-
The client assertion looks as follows:
{ "alg": "<<The algorithm used for signing.>>", "kid": "<<The thumbprint of the certificate.>>", "typ": "JWT" } { "iss": "<<This is the issuer of the token. For example, client ID of your application>>", "sub": "<<This is the subject identifier of the issuer. For example, client ID of your application>>", "exp": <<This is epoch time of the token expiration date/time>>, "iat": <<This is epoch time of the token issuance date/time>>, "jti": "<<This is an incremental unique value>>", "aud": "<<This is the audience that the ID token is intended for. For example, https:/<IS_HOST>:9446/oauth2/token" } <signature: For DCR, the client assertion is signed by the private key of the signing certificate. Otherwise the private signature of the application certificate is used.>eyJraWQiOiJEd01LZFdNbWo3UFdpbnZvcWZReVhWenlaNlEiLCJhbGciOiJQUzI1NiJ9.eyJzdWIiOiJIT1VrYVNieThEeWRuYmVJaEU3bHljYmtJSThhIiw iYXVkIjoiaHR0cHM6Ly9sb2NhbGhvc3Q6OTQ0Ni9vYXV0aDIvdG9rZW4iLCJpc3MiOiJIT1VrYVNieThEeWRuYmVJaEU3bHljYmtJSThhIiwiZXhwIjoxNjg 0MDk5ODEyLCJpYXQiOjE2ODQwOTk4MTMsImp0aSI6IjE2ODQwOTk4MTIifQ.EMZ2q3jciJ4MmrsH93kH_VGacrt2izbLaCBchGWiyUltdWwj3GwDMKfhpeMH tThd0DszwV8LUPKZaMT3wUSoH3adY2IBC8aa2GKeb_vaQB5b0ZO6WpYQ45y_xIttAVj56d6oPli8wN4MlJoJsFPUlaxQohCLunN43BxSr-kFgeFMj7ynEsVb QvuYuEiTppwTSyXltJmv70-nwpGU9UyuPCkXUsU53ShICrY0nC-3NUhY6oNpZclJP4MwG8mP4ZOvUIez_PSoP3AiaNithWhPCfLuKd68OLAReTBGdItqidsW Wnn8lPVbM2FLvehukHDCJhf9-ev1pdWIiwDSVDV7uQ -
Enter the value for
that you entered in the registration request. - To locate the value for
<CONSUMER_KEY>,- Go to
https://<APIM_HOST>:9443/devportaland click the Applications tab on top. - Select the application you registered and Production Keys > OAuth2 Tokens.
- You can view the unique value generated for
<CONSUMER_KEY>as follows: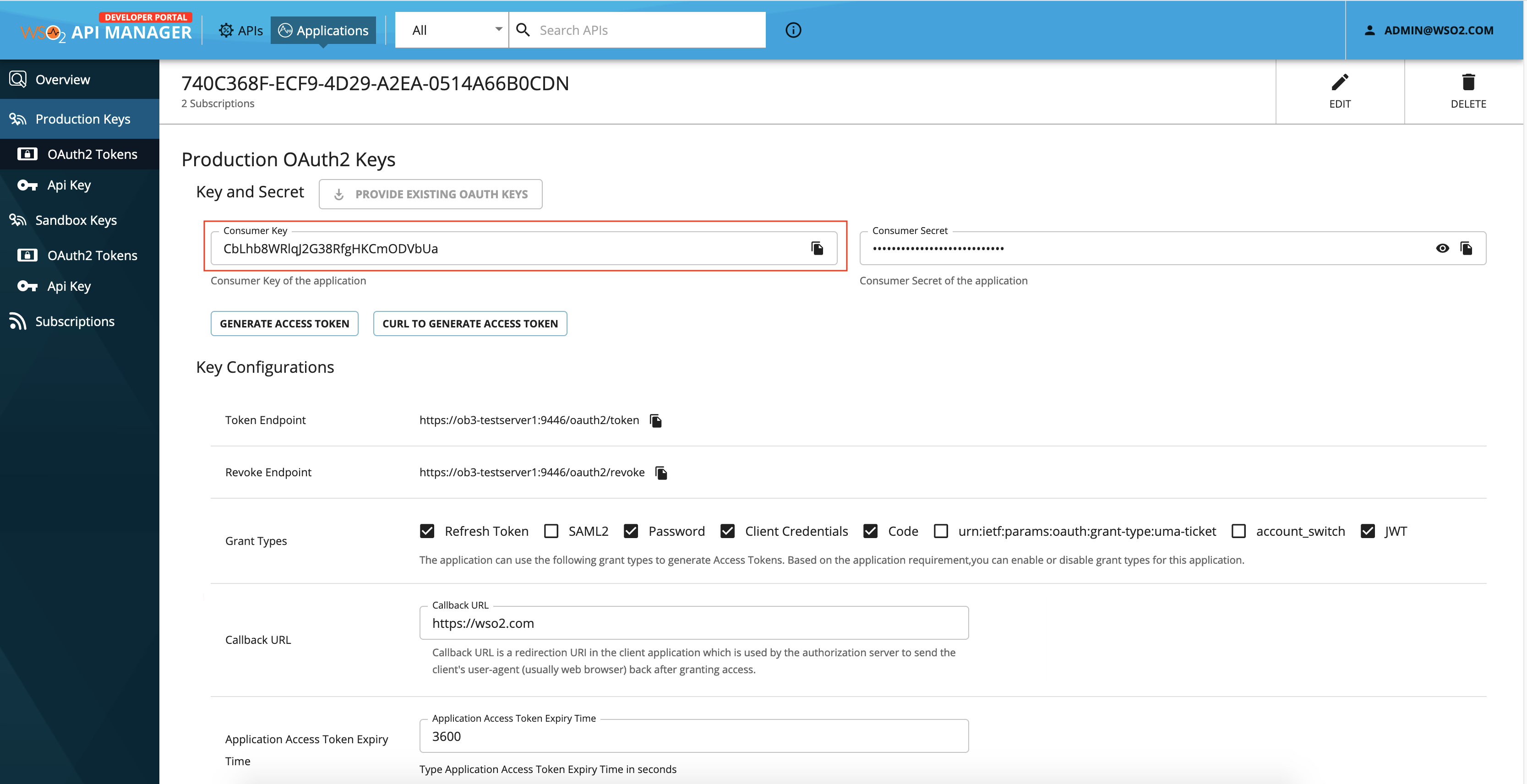
- Go to
Retrieve an application¶
The API allows the API consumer to retrieve the details for an application that has already been registered.
The request consists of one path parameter named Client ID that the API consumer wants to retrieve details for.
When invoking this API, use the attached
private key and
public certificate for Transport Layer Security purposes.
See the following sample request:
curl GET \https://<APIM_HOST>:8243/open-banking/0.1/register/<CLIENT_ID> \
-H 'Content-Type: application/json' \
-H 'Authorization: Bearer <APPLICATION_ACCESS_TOKEN>
--cert <TRANSPORT_PUBLIC_KEY_FILE_PATH> --key <TRANSPORT_PRIVATE_KEY_FILE_PATH>- If the request is successful and the
Client IDmatches the application to whom the application access token was issued, the bank returns details of the requested application. - If the
Client IDis unknown, the bank responds with anUnauthorizedstatus code.
You can find a sample response below:
{
"client_id": "CVY8RUWT3XVHAlRV_ZiA0dlB2Owa",
"client_id_issued_at": "1617198228",
"redirect_uris": [
"https://www.mockcompany.com.au/redirects/redirect1",
"https://www.mockcompany.com.au/redirects/redirect2"
],
"grant_types": [
"client_credentials",
"authorization_code",
"refresh_token",
"urn:ietf:params:oauth:grant-type:jwt-bearer"
],
"response_types": [
"code id_token"
],
"application_type": "web",
"id_token_signed_response_alg": "PS256",
"request_object_signing_alg": "PS256",
"scope": "bank:accounts.basic:read bank:accounts.detail:read bank:transactions:read bank:payees:read bank:regular_payments:read common:customer.basic:read common:customer.detail:read cdr:registration",
"software_id": "740C368F-ECF9-4D29-A2EA-0514A66B0CDN",
"token_endpoint_auth_method": "private_key_jwt",
"software_statement": "eyJhbGciOiJQUzI1NiIsImtpZCI6IkR3TUtkV01tajdQV2ludm9xZlF5WFZ6eVo2USIsInR5cCI6IkpXVCJ9.eyJpc3Mi
OiJjZHItcmVnaXN0ZXIiLCJpYXQiOjE1NzE4MDgxNjcsImV4cCI6MjE0NzQ4MzY0NiwianRpIjoiM2JjMjA1YTFlYmM5NDNmYmI2MjRiMTRmY2IyNDExOTYi
LCJvcmdfaWQiOiIzQjBCMEE3Qi0zRTdCLTRBMkMtOTQ5Ny1FMzU3QTcxRDA3QzgiLCJvcmdfbmFtZSI6Ik1vY2sgQ29tcGFueSBJbmMuIiwiY2xpZW50X25h
bWUiOiJNb2NrIFNvZnR3YXJlIiwiY2xpZW50X2Rlc2NyaXB0aW9uIjoiQSBtb2NrIHNvZnR3YXJlIHByb2R1Y3QgZm9yIHRlc3RpbmcgU1NBIiwiY2xpZW50
X3VyaSI6Imh0dHBzOi8vd3d3Lm1vY2tjb21wYW55LmNvbS5hdSIsInJlZGlyZWN0X3VyaXMiOlsiaHR0cHM6Ly93d3cuZ29vZ2xlLmNvbS9yZWRpcmVjdHMv
cmVkaXJlY3QxIiwiaHR0cHM6Ly93d3cuZ29vZ2xlLmNvbS9yZWRpcmVjdHMvcmVkaXJlY3QyIl0sImxvZ29fdXJpIjoiaHR0cHM6Ly93d3cubW9ja2NvbXBh
bnkuY29tLmF1L2xvZ29zL2xvZ28xLnBuZyIsInRvc191cmkiOiJodHRwczovL3d3dy5tb2NrY29tcGFueS5jb20uYXUvdG9zLmh0bWwiLCJwb2xpY3lfdXJp
IjoiaHR0cHM6Ly93d3cubW9ja2NvbXBhbnkuY29tLmF1L3BvbGljeS5odG1sIiwiandrc191cmkiOiJodHRwczovL2tleXN0b3JlLm9wZW5iYW5raW5ndGVz
dC5vcmcudWsvMDAxNTgwMDAwMUhRUXJaQUFYLzliNXVzRHBiTnRteERjVHpzN0d6S3AuandrcyIsInJldm9jYXRpb25fdXJpIjoiaHR0cHM6Ly9naXN0Lmdp
dGh1YnVzZXJjb250ZW50LmNvbS9pbWVzaDk0LzMxNzJlMmU0NTc1N2NkYTA4ZWMyNzI3ZjkwYjcyY2VkL3Jhdy9mZjBkM2VhYmU0Y2RkY2U0N2VlYzAyMjhm
NTkyMTc1MjIzZGQ5MmIyL3dzbzItYXUtZGNyLWRlbW8uandrcyIsInJlY2lwaWVudF9iYXNlX3VyaSI6Imh0dHBzOi8vd3d3Lm1vY2tjb21wYW55LmNvbS5h
dSIsInNvZnR3YXJlX2lkIjoiNzQwQzM2OEYtRUNGOS00RDI5LUEyRUEtMDUxNEE2NkIwQ0ROIiwic29mdHdhcmVfcm9sZXMiOiJkYXRhLXJlY2lwaWVudC1z
b2Z0d2FyZS1wcm9kdWN0Iiwic2NvcGUiOiJiYW5rOmFjY291bnRzLmJhc2ljOnJlYWQgYmFuazphY2NvdW50cy5kZXRhaWw6cmVhZCBiYW5rOnRyYW5zYWN0
aW9uczpyZWFkIGJhbms6cGF5ZWVzOnJlYWQgYmFuazpyZWd1bGFyX3BheW1lbnRzOnJlYWQgY29tbW9uOmN1c3RvbWVyLmJhc2ljOnJlYWQgY29tbW9uOmN1
c3RvbWVyLmRldGFpbDpyZWFkIGNkcjpyZWdpc3RyYXRpb24ifQ.bKtuQ9AM5ekKx1l3R36dkJi423jagZvrKflNzZjZt8vFIGgBYp10g0RTYkL4uvJPICcfo
6e01tP4nMd1Z47TvHdMdAxk-1Mr6QpxJQFeVRrtI2MHPiCNrD-0b0-2l6VxN5YO-ggJq1wouhecKxR-HnHLrpoO6l9Zsrnouy4rQbznDFsQmvX2N7n-rKUnD
93z_TojwLqIIECKCAZhlJpjgOMIi4bZoe4-y_1zkUS9D-VB2ZA-eftEQfsD1-aQ9mNsn-uFmWSACsaTYOMd6xmsoog5dVd29i2HEKXpiLNl02XeMRlFWUHmJ
vOFwerKQESFMV2evdg1gyCR5odG_8dxXg"
} Update an application¶
The API allows the API consumer to request the bank to modify one or more attributes related to an existing application.
The API consumer submits Client ID as a path parameter and a JWS payload that describes the characteristics of the
application to be modified. This must include all the claims, including the ones that will not be modified.
When invoking this API, use the attached
private key and
public certificate for Transport Layer Security purposes.
See the following sample request:
curl PUT \https://<APIM_HOST>:8243/open-banking/0.1/register/<CLIENT_ID> \
-H 'Content-Type: application/jwt' \
-H 'Authorization: Bearer <APPLICATION_ACCESS_TOKEN> \
--cert <TRANSPORT_PUBLIC_KEY_FILE_PATH> --key <TRANSPORT_PRIVATE_KEY_FILE_PATH>
-d 'eyJ0eXAiOiJKV1QiLCJhbGciOiJQUzI1NiIsImtpZCI6IkR3TUtkV01tajdQV2ludm9xZlF5WFZ6eVo2USJ9.eyJpc3MiOiI3NDBDMzY4Ri1FQ0Y5LTREMjktQTJFQS0wNTE0QTY2QjBDRE4iLCJpYXQiOjE1NzE4MDgxNjcsImV4cCI6MjE0NzQ4MzY0NiwianRpIjoiMzc3NDdjZDFjMTA1NDU2OTlmNzU0YWRmMjhiNzNlMzEiLCJhdWQiOiJodHRwczovL3NlY3VyZS5hcGkuZGF0YWhvbGRlci5jb20vaXNzdWVyIiwicmVkaXJlY3RfdXJpcyI6WyJodHRwczovL3d3dy5tb2NrY29tcGFueS5jb20uYXUvcmVkaXJlY3RzL3JlZGlyZWN0MSIsImh0dHBzOi8vd3d3Lm1vY2tjb21wYW55LmNvbS5hdS9yZWRpcmVjdHMvcmVkaXJlY3QyIl0sInRva2VuX2VuZHBvaW50X2F1dGhfc2lnbmluZ19hbGciOiJQUzI1NiIsInRva2VuX2VuZHBvaW50X2F1dGhfbWV0aG9kIjoidGxzX2NsaWVudF9hdXRoIiwiZ3JhbnRfdHlwZXMiOlsiY2xpZW50X2NyZWRlbnRpYWxzIiwiYXV0aG9yaXphdGlvbl9jb2RlIiwicmVmcmVzaF90b2tlbiIsInVybjppZXRmOnBhcmFtczpvYXV0aDpncmFudC10eXBlOmp3dC1iZWFyZXIiXSwicmVzcG9uc2VfdHlwZXMiOlsiY29kZSBpZF90b2tlbiJdLCJhcHBsaWNhdGlvbl90eXBlIjoid2ViIiwiaWRfdG9rZW5fc2lnbmVkX3Jlc3BvbnNlX2FsZyI6IlBTMjU2IiwiaWRfdG9rZW5fZW5jcnlwdGVkX3Jlc3BvbnNlX2FsZyI6IlJTQS1PQUVQIiwiaWRfdG9rZW5fZW5jcnlwdGVkX3Jlc3BvbnNlX2VuYyI6IkEyNTZHQ00iLCJyZXF1ZXN0X29iamVjdF9zaWduaW5nX2FsZyI6IlBTMjU2Iiwic29mdHdhcmVfc3RhdGVtZW50IjoiZXlKaGJHY2lPaUpRVXpJMU5pSXNJbXRwWkNJNklrUjNUVXRrVjAxdGFqZFFWMmx1ZG05eFpsRjVXRlo2ZVZvMlVTSXNJblI1Y0NJNklrcFhWQ0o5LmV5SnBjM01pT2lKalpISXRjbVZuYVhOMFpYSWlMQ0pwWVhRaU9qRTFOekU0TURneE5qY3NJbVY0Y0NJNk1qRTBOelE0TXpZME5pd2lhblJwSWpvaU0ySmpNakExWVRGbFltTTVORE5tWW1JMk1qUmlNVFJtWTJJeU5ERXhPVFlpTENKdmNtZGZhV1FpT2lJelFqQkNNRUUzUWkwelJUZENMVFJCTWtNdE9UUTVOeTFGTXpVM1FUY3hSREEzUXpnaUxDSnZjbWRmYm1GdFpTSTZJazF2WTJzZ1EyOXRjR0Z1ZVNCSmJtTXVJaXdpWTJ4cFpXNTBYMjVoYldVaU9pSk5iMk5ySUZOdlpuUjNZWEpsSWl3aVkyeHBaVzUwWDJSbGMyTnlhWEIwYVc5dUlqb2lRU0J0YjJOcklITnZablIzWVhKbElIQnliMlIxWTNRZ1ptOXlJSFJsYzNScGJtY2dVMU5CSWl3aVkyeHBaVzUwWDNWeWFTSTZJbWgwZEhCek9pOHZkM2QzTG0xdlkydGpiMjF3WVc1NUxtTnZiUzVoZFNJc0luSmxaR2x5WldOMFgzVnlhWE1pT2xzaWFIUjBjSE02THk5M2QzY3VaMjl2WjJ4bExtTnZiUzl5WldScGNtVmpkSE12Y21Wa2FYSmxZM1F4SWl3aWFIUjBjSE02THk5M2QzY3VaMjl2WjJ4bExtTnZiUzl5WldScGNtVmpkSE12Y21Wa2FYSmxZM1F5SWwwc0lteHZaMjlmZFhKcElqb2lhSFIwY0hNNkx5OTNkM2N1Ylc5amEyTnZiWEJoYm5rdVkyOXRMbUYxTDJ4dloyOXpMMnh2WjI4eExuQnVaeUlzSW5SdmMxOTFjbWtpT2lKb2RIUndjem92TDNkM2R5NXRiMk5yWTI5dGNHRnVlUzVqYjIwdVlYVXZkRzl6TG1oMGJXd2lMQ0p3YjJ4cFkzbGZkWEpwSWpvaWFIUjBjSE02THk5M2QzY3ViVzlqYTJOdmJYQmhibmt1WTI5dExtRjFMM0J2YkdsamVTNW9kRzFzSWl3aWFuZHJjMTkxY21raU9pSm9kSFJ3Y3pvdkwydGxlWE4wYjNKbExtOXdaVzVpWVc1cmFXNW5kR1Z6ZEM1dmNtY3VkV3N2TURBeE5UZ3dNREF3TVVoUlVYSmFRVUZZTHpsaU5YVnpSSEJpVG5SdGVFUmpWSHB6TjBkNlMzQXVhbmRyY3lJc0luSmxkbTlqWVhScGIyNWZkWEpwSWpvaWFIUjBjSE02THk5bmFYTjBMbWRwZEdoMVluVnpaWEpqYjI1MFpXNTBMbU52YlM5cGJXVnphRGswTHpNeE56SmxNbVUwTlRjMU4yTmtZVEE0WldNeU56STNaamt3WWpjeVkyVmtMM0poZHk5bVpqQmtNMlZoWW1VMFkyUmtZMlUwTjJWbFl6QXlNamhtTlRreU1UYzFNakl6WkdRNU1tSXlMM2R6YnpJdFlYVXRaR055TFdSbGJXOHVhbmRyY3lJc0luSmxZMmx3YVdWdWRGOWlZWE5sWDNWeWFTSTZJbWgwZEhCek9pOHZkM2QzTG0xdlkydGpiMjF3WVc1NUxtTnZiUzVoZFNJc0luTnZablIzWVhKbFgybGtJam9pTnpRd1F6TTJPRVl0UlVOR09TMDBSREk1TFVFeVJVRXRNRFV4TkVFMk5rSXdRMFJPSWl3aWMyOW1kSGRoY21WZmNtOXNaWE1pT2lKa1lYUmhMWEpsWTJsd2FXVnVkQzF6YjJaMGQyRnlaUzF3Y205a2RXTjBJaXdpYzJOdmNHVWlPaUppWVc1ck9tRmpZMjkxYm5SekxtSmhjMmxqT25KbFlXUWdZbUZ1YXpwaFkyTnZkVzUwY3k1a1pYUmhhV3c2Y21WaFpDQmlZVzVyT25SeVlXNXpZV04wYVc5dWN6cHlaV0ZrSUdKaGJtczZjR0Y1WldWek9uSmxZV1FnWW1GdWF6cHlaV2QxYkdGeVgzQmhlVzFsYm5Sek9uSmxZV1FnWTI5dGJXOXVPbU4xYzNSdmJXVnlMbUpoYzJsak9uSmxZV1FnWTI5dGJXOXVPbU4xYzNSdmJXVnlMbVJsZEdGcGJEcHlaV0ZrSW4wLlM2QjYwbmI3S2doVnJOaWhNRVM4T0k4d1BaRkUzSER6NEVucGt2ckNCTDJPdVlOc2J3SGc4LXpQdWM0LVU0dlZEWmozXzNKYUNkbERQZy1JNHNhTFZkLTJWcmhXeEJoWkNLLXVScUs1WklXSkdYanYzU3RQRDhfMkZORlZMdGJjTk4yVjNwVHkxdG5haXROZkgwZjhoYklhUkV6M29HTmh5NVNPS1NlNTNZVjRzV0ZxSVJBeC1zclVqRk4yclF0cldEMTRDSmtCd25TcnB5bWMxVlJBaURsdmNKNWF6UjhMVEJhelRfXzltUjRiMlBSelRhSjdnOTBqUklBSzlmdUs4Zy1qX1FoWVhjNXgxX2F4WWJZd3g2Q2dUc0QxWXo1N1F5U2RhU0JiaE5hZERfNDZEWEUtTnZITHVObFVhQVJGekFHaFhWZTJ1Rm5LQ0pROWw3VGM4QSJ9.OAPxUCCpmNMREraChiDyNrddPtHiMvuAePb-8FOZJJWOvzpR8h6nCTIbpienhs2PBvGDqJ_0CaoXLLMAXcEhJuBQZzee_BfWlDh3o2RgJj6yL9saM7WdddUOD4tt7mxghNVUx2tmQqxiAwwQjlYQVfzu6vjlCUQofaQj8baZx7wTWXbIC2vw-IoEY2TmNSps34q62LTTfIqJQmPqwc39iLsuWgU3_M1Zry9WwyMIKVYOicKtRXLRRh5s76V7IGUHBGT6qpVpOvZAUIKgdKykqmjCpot0dDTX1F43-DSdGVRl2p7I2lDC1IDIlD0GZ3N0w_LzqM-66rjZi2BSLrOp5Q'- If the application is successfully modified, the bank responds with a JSON payload.
- If the
Client IDis unknown, the bank responds with anUnauthorizedstatus code. - If the modification is unsuccessful, the bank responds with an error payload.
You can find a sample response below:
{
"client_id": "CVY8RUWT3XVHAlRV_ZiA0dlB2Owa",
"client_id_issued_at": "1617198228",
"redirect_uris": [
"https://www.mockcompany.com.au/redirects/redirect1",
"https://www.mockcompany.com.au/redirects/redirect2"
],
"grant_types": [
"client_credentials",
"authorization_code",
"refresh_token",
"urn:ietf:params:oauth:grant-type:jwt-bearer"
],
"response_types": [
"code id_token"
],
"application_type": "web",
"id_token_signed_response_alg": "PS256",
"request_object_signing_alg": "PS256",
"scope": "bank:accounts.basic:read bank:accounts.detail:read bank:transactions:read bank:payees:read bank:regular_payments:read common:customer.basic:read common:customer.detail:read",
"software_id": "740C368F-ECF9-4D29-A2EA-0514A66B0CDN",
"token_endpoint_auth_method": "tls_client_auth",
"software_statement": "eyJhbGciOiJQUzI1NiIsImtpZCI6IkR3TUtkV01tajdQV2ludm9xZlF5WFZ6eVo2USIsInR5cCI6IkpXVCJ9.eyJpc3Mi
OiJjZHItcmVnaXN0ZXIiLCJpYXQiOjE1NzE4MDgxNjcsImV4cCI6MjE0NzQ4MzY0NiwianRpIjoiM2JjMjA1YTFlYmM5NDNmYmI2MjRiMTRmY2IyNDExOTYi
LCJvcmdfaWQiOiIzQjBCMEE3Qi0zRTdCLTRBMkMtOTQ5Ny1FMzU3QTcxRDA3QzgiLCJvcmdfbmFtZSI6Ik1vY2sgQ29tcGFueSBJbmMuIiwiY2xpZW50X25h
bWUiOiJNb2NrIFNvZnR3YXJlIiwiY2xpZW50X2Rlc2NyaXB0aW9uIjoiQSBtb2NrIHNvZnR3YXJlIHByb2R1Y3QgZm9yIHRlc3RpbmcgU1NBIiwiY2xpZW50
X3VyaSI6Imh0dHBzOi8vd3d3Lm1vY2tjb21wYW55LmNvbS5hdSIsInJlZGlyZWN0X3VyaXMiOlsiaHR0cHM6Ly93d3cuZ29vZ2xlLmNvbS9yZWRpcmVjdHMv
cmVkaXJlY3QxIiwiaHR0cHM6Ly93d3cuZ29vZ2xlLmNvbS9yZWRpcmVjdHMvcmVkaXJlY3QyIl0sImxvZ29fdXJpIjoiaHR0cHM6Ly93d3cubW9ja2NvbXBh
bnkuY29tLmF1L2xvZ29zL2xvZ28xLnBuZyIsInRvc191cmkiOiJodHRwczovL3d3dy5tb2NrY29tcGFueS5jb20uYXUvdG9zLmh0bWwiLCJwb2xpY3lfdXJp
IjoiaHR0cHM6Ly93d3cubW9ja2NvbXBhbnkuY29tLmF1L3BvbGljeS5odG1sIiwiandrc191cmkiOiJodHRwczovL2tleXN0b3JlLm9wZW5iYW5raW5ndGVz
dC5vcmcudWsvMDAxNTgwMDAwMUhRUXJaQUFYLzliNXVzRHBiTnRteERjVHpzN0d6S3AuandrcyIsInJldm9jYXRpb25fdXJpIjoiaHR0cHM6Ly9naXN0Lmdp
dGh1YnVzZXJjb250ZW50LmNvbS9pbWVzaDk0LzMxNzJlMmU0NTc1N2NkYTA4ZWMyNzI3ZjkwYjcyY2VkL3Jhdy9mZjBkM2VhYmU0Y2RkY2U0N2VlYzAyMjhm
NTkyMTc1MjIzZGQ5MmIyL3dzbzItYXUtZGNyLWRlbW8uandrcyIsInJlY2lwaWVudF9iYXNlX3VyaSI6Imh0dHBzOi8vd3d3Lm1vY2tjb21wYW55LmNvbS5h
dSIsInNvZnR3YXJlX2lkIjoiNzQwQzM2OEYtRUNGOS00RDI5LUEyRUEtMDUxNEE2NkIwQ0ROIiwic29mdHdhcmVfcm9sZXMiOiJkYXRhLXJlY2lwaWVudC1z
b2Z0d2FyZS1wcm9kdWN0Iiwic2NvcGUiOiJiYW5rOmFjY291bnRzLmJhc2ljOnJlYWQgYmFuazphY2NvdW50cy5kZXRhaWw6cmVhZCBiYW5rOnRyYW5zYWN0
aW9uczpyZWFkIGJhbms6cGF5ZWVzOnJlYWQgYmFuazpyZWd1bGFyX3BheW1lbnRzOnJlYWQgY29tbW9uOmN1c3RvbWVyLmJhc2ljOnJlYWQgY29tbW9uOmN1
c3RvbWVyLmRldGFpbDpyZWFkIn0.S6B60nb7KghVrNihMES8OI8wPZFE3HDz4EnpkvrCBL2OuYNsbwHg8-zPuc4-U4vVDZj3_3JaCdlDPg-I4saLVd-2VrhW
xBhZCK-uRqK5ZIWJGXjv3StPD8_2FNFVLtbcNN2V3pTy1tnaitNfH0f8hbIaREz3oGNhy5SOKSe53YV4sWFqIRAx-srUjFN2rQtrWD14CJkBwnSrpymc1VRA
iDlvcJ5azR8LTBazT__9mR4b2PRzTaJ7g90jRIAK9fuK8g-j_QhYXc5x1_axYbYwx6CgTsD1Yz57QySdaSBbhNadD_46DXE-NvHLuNlUaARFzAGhXVe2uFnK
CJQ9l7Tc8A"
}Delete an application¶
The API allows the API consumer to request the bank to delete an existing application. The request consists of the
Client ID of the application, which should be deleted. When invoking this API, use the attached
private key and
public certificate for Transport Layer Security purposes.
See the following sample request:
curl DELETE \https://<APIM_HOST>:8243/open-banking/0.1/register/<CLIENT_ID> \
-H 'Authorization: Bearer <APPLICATION_ACCESS_TOKEN> \
--cert <TRANSPORT_PUBLIC_KEY_FILE_PATH> --key <TRANSPORT_PRIVATE_KEY_FILE_PATH>- If the request is successful and the
Client IDmatches the application, the bank deletes the application and invalidates long-lived access tokens that were issued to the application. - If the
Client IDis unknown, the bank responds with anUnauthorizedstatus code.
If the deletion is successful you will get a 204 No Content response.
Top